Threat Assessment and Management Tools
It has been recognized that the most effective threat assessment and management practice is informed by structured professional judgment. Threat Assessment and Management professionals are therefore encouraged to use structured evaluative devices or procedures to inform their practice [see Guidelines for more information].
We have listed below some tools and guidelines which have been developed for application in Threat Assessment and Management practice. By listing these products, AETAP are not endorsing their validity; we are simply highlighting their potential utility for our TAM community to consider in more detail.
There are advantages and disadvantages to most of those listed, and practitioners are therefore reminded of the need to inform themselves of the reliability and validity of the tools in relation to their task in hand before utilising them.
Some of the tools have been developed for the purposes of risk assessment and an objective evaluation of them can be found on the Scottish Risk Management Authority (RMA)’s RATED directory (https://www.rma.scot/research/rated/). We have also provided links where possible to research which has tested some tools in practice.
Visitors to this page are also reminded of the need to seek adequate training before using any of the tools listed. Some of the tools listed require completion of formal training programmes prior to use.
We have listed the tools under our threat categories. It is fully acknowledged that these categories are not mutually exclusive, but this is reflective of the practice of threat assessment and management; pigeonholing issues into one theme or area of concern is neither appropriate nor necessary. There will therefore be duplication across the category pages. The categories or themes therefore merely provide an initial signposting for where members may wish to begin their search for useful and relevant information on any topic.
Tools included under threat categories:
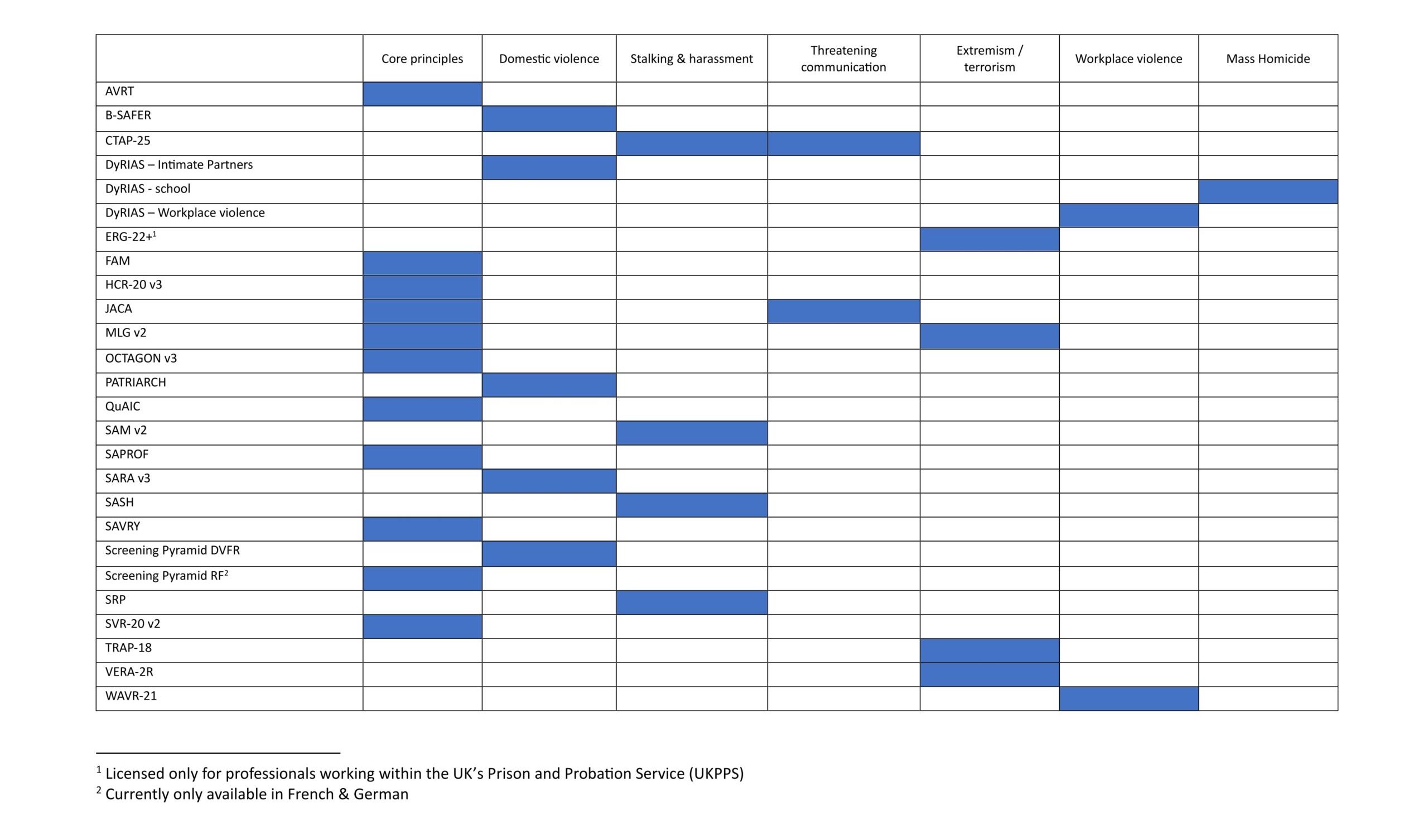
Further information and access to certain tools are available to AETAP members in the password-protected member area.
Core Principles of Threat Assessment and Management
This section covers the key principles of threat assessment and management, and outlines the differences between this field and risk assessment. It covers the theoretical constructs that underpin TAM and offers practice advice including guidance on information gathering, (investigative) interviewing, ethical issues, fear management, etc.
Domestic Violence, including Honour-Based Violence
This section focuses on targeted violence & threatening behaviour within intimate relationships. It covers violence committed by intimate and ex-intimate partners, gender-based violence or femicide, and domestic violence (including violence perpetrated by family members, e.g., sons, mothers, etc.).
This section covers all aspects of stalking behaviour and harassment. There are various legal definitions of stalking and harassment across Europe, but within AETAP we broadly define this area as activity which presents as a repeated pattern of unwanted behaviour which causes distress and feels threatening to the intended target.
This section covers any method of communication which is implicitly or explicitly threatening. This includes behaviour directed towards a known, unknown or public figure, and comprises both online and IRL media.
This section covers ideologically-driven targeted violence. As with all the other sections, it encompasses the pathways that lead to this activity, including radicalisation.
Workplace Violence & Insider Threat
This section covers concerning and unwarranted behaviour which occurs within the workplace. It includes violence targeted against senior executives, management and workforce, and encompasses insider threat.
This section covers targeted, explicit violence perpetrated against multiple individuals, and threats thereof.
Most people with a mental disorder will not exhibit threatening behaviour; however, when they do, it is essential that we understand how to respond appropriately and adopt supportive intervention practices. This section therefore comprises information about the role of mental illness, ill-health and personality disorder in targeted violence and good practice guidance.
This final miscellaneous category covers new areas which are emerging within the TAM field, e.g., Artificial Intelligence and Machine Learning.
